Assessing Security Header Vulnerabilities in Penetration Test Findings

Table of Content
- Introduction
- Common security header penetration test finding
- Challenges in assessing security header vulnerabilities
- Solutions for addressing challenges in assessing security header vulnerabilities
- Step-by-Step Assessment Guide for Security Header Vulnerabilities
- Conclusion
Introduction
Security headers are a critical component of web application security, providing an added layer of protection against a range of attacks. However, missing or surplus security headers are a common finding in penetration testing, and determining their impact can be a challenging task. In this blog post, we’ll explore common security header vulnerabilities, the challenges involved in assessing them, and provide a step-by-step guide for determining whether a penetration test finding related to security headers represents a genuine vulnerability or not, and how to take appropriate actions based on the assessment.
Security Headers and Webapp Security
Before we dive into assessing vulnerabilities of security headers, let’s shortly talk about what security header are.
Security headers are a set of HTTP response headers that provide additional security protections for web applications. They were first introduced in 2004 as a response to the growing number of web-based attacks targeting vulnerabilities in web browsers and web applications. The initial set of headers were created by the Internet Engineering Task Force (IETF) and have since been expanded by various organizations and companies.
Security headers are used to protect web applications from a variety of attacks, such as cross-site scripting (XSS), clickjacking, and content sniffing. They work by adding additional information to HTTP responses that provide guidance to web browsers on how to handle certain types of content and behavior.
Importance of Penetration Testing
Penetration testing is a crucial component of any organization’s security posture, providing valuable insights into the vulnerabilities and weaknesses of their web applications. One of the most common findings in penetration testing is missing or surplus security headers, which can leave web applications vulnerable to a range of attacks. However, determining whether these security headers represent a genuine vulnerability can be challenging, requiring a deep understanding of the web application’s context and the potential impact of the missing or surplus security header.
Common security header penetration test finding
Common security header vulnerabilities are a frequent finding during penetration testing, which can indicate a weakness in a web application’s security posture. There are two common types of security header vulnerabilities: missing headers and surplus headers. Missing headers are HTTP headers that are not present or configured correctly on a web application, leaving it vulnerable to attacks. surplus headers, on the other hand, are headers that are unnecessary for a web application’s security and may even introduce new vulnerabilities.
Missing Security Headers
Missing security headers are the most common finding in penetration testing, and they can have a significant impact on the security of web applications. Here are some examples:
- Content Security Policy (CSP)
A CSP header defines a whitelist of trusted sources for content, scripts, and other resources. If missing or misconfigured, an attacker could inject malicious code into a web page, leading to cross-site scripting attacks, data exfiltration, and other security risks. - HTTP Strict Transport Security (HSTS)
HSTS is a security header that instructs browsers to only communicate with a web server over a secure HTTPS connection. Without this header, an attacker could intercept and manipulate traffic between the client and server, potentially stealing sensitive information or injecting malicious code. - X-Frame-Options (XFO)
XFO is a security header that prevents clickjacking attacks, where an attacker tricks a user into clicking on a button or link that triggers a malicious action. Without this header, an attacker could embed a vulnerable web page inside a frame, and manipulate it to trick users into performing actions they didn’t intend to do.
Surplus Security Headers
Another common security header related penetration test finding is surplus headers. These are headers that are not or no longer relevant or necessary for the application’s current configuration, but are still present in the server response. Examples of such headers include the CORS header, which is used to control access to resources from other domains, and may allow cross-site scripting (XSS) attacks if not properly configured. Other headers that may be unnecessary or redundant include the X-Powered-By header and Server header, which reveal information about the web server and could be exploited by attackers.
It’s important to keep in mind that these are just a few instances of security header vulnerabilities that commonly occur. There might be other headers that could be crucial to the security posture of your web application. In the following section, we will examine the difficulties in assessing security header vulnerabilities and how to decide whether a missing or redundant header poses a real security threat.
Challenges in assessing security header vulnerabilities
While missing or surplus security headers may seem like straightforward vulnerabilities, there are several challenges involved in assessing their impact and severity. One of the main challenges is the risk of false positives and false negatives in automated testing tools. Automated tools can be useful for quickly identifying missing headers, but they may not accurately assess the impact of the missing header on the web application.
Contextual knowledge is also critical in assessing security header vulnerabilities. For example, a missing CSP header may be less severe if the web application is using other security measures, such as a Content Delivery Network (CDN) or other types of input validation. Conversely, a missing CSP header could be catastrophic if the web application is handling sensitive data, such as financial information or personal data.
Another challenge in assessing security header vulnerabilities is the limited time and resources available for testing. Penetration testers may not have sufficient time to thoroughly test every aspect of the web application, including security headers. As a result, they may miss critical vulnerabilities, including those related to security headers.
In the next sections, we will discuss potential solutions for addressing these challenges, including manual testing, a risk-based approach to vulnerability assessment, and close collaboration with developers and security experts. By adopting these strategies, organizations can gain a more accurate understanding of their web application’s security posture and reduce the risk of security breaches.
Solutions for addressing challenges in assessing security header vulnerabilities
In this section, we’ll explore some solutions for overcoming the challenges involved in assessing security header vulnerabilities. These solutions can help improve the accuracy and effectiveness of vulnerability assessments, and ensure that your web application is better protected against potential attacks.
Performing manual testing and analysis
Performing manual testing and analysis is another solution for addressing the challenges involved in assessing security header vulnerabilities. While automated tools can be helpful in identifying potential vulnerabilities, they often generate false positives or false negatives. Manual testing and analysis can help to provide a more accurate and comprehensive assessment of the security posture of a web application.
Manual testing involves a human tester reviewing the web application to identify potential vulnerabilities. This can include checking for the presence or absence of security headers, as well as testing the functionality of the headers to ensure that they are providing the intended security protections. Manual testing can also help to identify vulnerabilities that may not be detected by automated tools, such as issues related to the specific context or configuration of the web application.
Manual analysis involves reviewing the results of automated testing to identify false positives or false negatives, as well as to provide additional context and information that may not be captured by automated tools. This can include reviewing the source code of the web application to identify potential vulnerabilities, as well as reviewing the logs and other data generated by the web application to identify potential security issues.
Overall, performing manual testing and analysis can help to provide a more accurate and comprehensive assessment of the security posture of a web application, and can help to identify vulnerabilities that may be missed by automated tools alone. However, manual testing and analysis can be time-consuming and resource-intensive, so it may not be practical for all organizations or web applications. A risk-based approach to vulnerability assessment can help to prioritize manual testing and analysis efforts for the most critical vulnerabilities.
Employing a risk-based approach to vulnerability assessment
Employing a risk-based approach to vulnerability assessment is a proactive way of dealing with security header vulnerabilities. By prioritizing the most critical security headers, a risk-based approach can help organizations allocate their resources more efficiently and focus on addressing the most pressing security risks.
To employ a risk-based approach to vulnerability assessment, organizations should first identify the most important security headers for their web application based on the potential impact of an attack. This can be done by considering factors such as the type of application, the types of users accessing it, and the data being transmitted.
Once the most important security headers have been identified, organizations should perform a thorough risk assessment to identify potential vulnerabilities and prioritize them based on the level of risk they pose. This involves evaluating the likelihood of an attack, the potential impact of an attack, and the resources required to mitigate the vulnerability.
By employing a risk-based approach to vulnerability assessment, organizations can focus their resources on the most critical vulnerabilities and address them in a timely and efficient manner. This can help to reduce the risk of a successful attack and ensure that web applications are secure against a wide range of threats.
Collaborating with developers and security experts
Collaborating with developers and security experts can be an effective solution for addressing challenges in assessing security header vulnerabilities. Developers and security experts have different areas of expertise that can complement each other in the vulnerability assessment process.
Developers have a deep understanding of the web application’s code and architecture, which is critical for identifying potential vulnerabilities related to security headers. They can also help in the implementation of security headers in the web application, ensuring that they are properly configured and optimized for the application’s context.
Security experts, on the other hand, have extensive knowledge of security best practices and the latest threats and vulnerabilities. They can provide guidance on which security headers to implement based on the web application’s specific needs and potential risks. They can also help in reviewing the results of automated testing tools, providing additional context and expertise to determine the severity of potential vulnerabilities.
By collaborating with both developers and security experts, organizations can take a holistic approach to vulnerability assessment, leveraging the strengths of both teams. This can lead to more accurate and effective vulnerability assessment results, ultimately improving the overall security posture of the web application.
Applying Threat Modeling to Identify Security Requirements
Applying threat modeling to identify requirements for security headers is another proactive approach to ensuring the effectiveness of security headers in mitigating potential threats. Threat modeling involves identifying and assessing the potential threats and risks to the application, as well as the potential vulnerabilities in the system that could be exploited by an attacker. By using this approach, security teams can determine which security headers are necessary and which headers are not needed, based on the identified threats and risks.
Threat modeling can help prioritize which security headers should be implemented, based on their potential impact on mitigating identified threats. For example, if the application is vulnerable to cross-site scripting (XSS) attacks, the Content-Security-Policy (CSP) header would be a high priority. By prioritizing security headers in this way, security teams can focus their resources on implementing the headers that will have the most impact on reducing risk.
In addition to prioritizing security headers, threat modeling can also help identify potential gaps in security controls and identify additional security measures that should be implemented. By collaborating with developers and other stakeholders, security teams can ensure that the identified security headers are properly implemented and configured to effectively mitigate the identified threats.
Step-by-Step Assessment Guide for Security Header Vulnerabilities
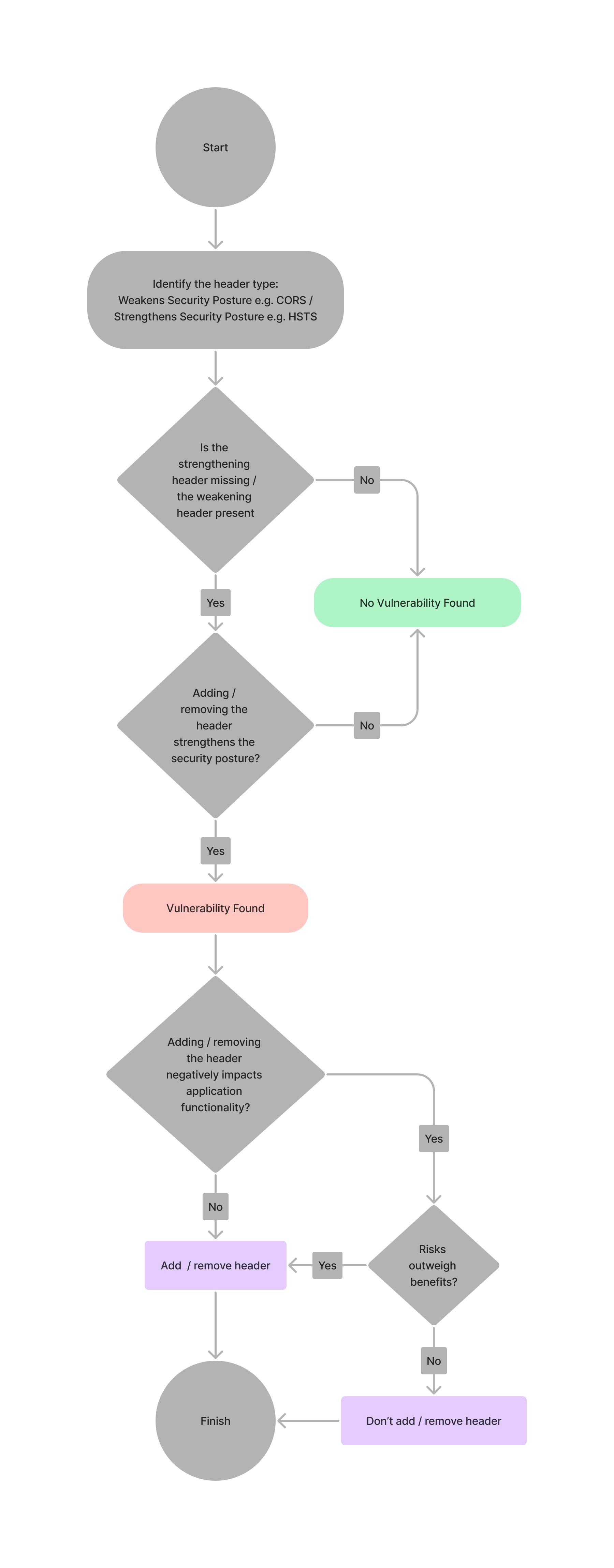
Fig.1 - Assessment Guide for Security Header Vulnerabilities
By following this step-by-step assessment guide, you can ensure that you are making informed decisions when it comes to security headers and their impact on your application’s security posture. This approach allows you to assess each header on a case-by-case basis, making sure that you are not compromising security or functionality.
Conclusion
In this blog post, we discussed the importance of assessing security header vulnerabilities in web applications and provided a step-by-step guide for determining whether a penetration test finding related to security headers represents a genuine vulnerability or not, and how to take appropriate actions based on the assessment.
To recap, the assessment guide involves identifying whether the header weakens or strengthens the security posture, whether the strengthening header is missing or the weakening header is present, and whether adding or removing the header strengthens the security posture or negatively impacts application functionality. Based on these factors, appropriate actions can be taken to address the vulnerability, including adding or removing the header.
It is essential to address security header vulnerabilities in web applications as they can protect against a variety of attacks, such as cross-site scripting (XSS), clickjacking, and content sniffing. By adding security headers to HTTP responses, web applications can provide additional security protections, guiding web browsers on how to handle certain types of content and behavior.
While security headers can provide crucial protection against various attacks, it’s important to note that they are not a panacea. It’s equally, if not more important to address the underlying vulnerabilities that the headers are designed to protect against. Relying solely on headers to shield an application from attacks without addressing the root cause of the vulnerabilities is not a sustainable long-term solution. Therefore, it’s crucial to implement a comprehensive security program that encompasses both the application and the headers to provide maximum protection against potential threats.
In conclusion, improving web application security is crucial in today’s threat landscape. Organizations should regularly assess their web applications for security header vulnerabilities and take appropriate measures to mitigate risks. This can be achieved by collaborating with developers and security experts, employing a risk-based approach to vulnerability assessment, and performing manual testing and analysis. By prioritizing web application security, organizations can safeguard sensitive information, protect against cyber threats, and maintain trust with their users.